Docker Login
Many projects keep the docker images on registries hosted by providers like AWS. This article talks about how to login to the registry so that you can pull images either with docker pull command or from within Kubernetes.
A token is needed from AWS to be used from docker as a password. The token is obtained with the following command:
aws ecr get-login-password --region us-east-2 --profile dockerThe profile called “docker” must have the AWS key and secret key that would allow access to the registry.
After this is obtained, the token can be passed in the input stream of the docker login command as follows
aws ecr get-login-password --region us-east-2 --profile docker | \
docker login --username AWS --password-stdin \
999999999.dkr.ecr.us-east-2.amazonaws.comThose “999” represent the account number; us-east-2 is the region. They must correspond to the registry to be accessed. Following the above command the docker is logged in. On unix under the .~/.docker folder there will be a file called config.json with the credentials. In other operating systems like windows, for example, the config.json file contains just part of the information, the actual token is stored in some kind of operating system vault and cannot be accessed easily.
In order to resolve this, create as config.json file with the template below and under the “auth” entry place the token obtained with aws ecr command. The token is already base64. Here is the template:
{
"auths": {
"999999.dkr.ecr.us-east-2.amazonaws.com": {
"auth": "...."
}
}
Kubernetes
Kubernetes pulls the images from the registry in order to create deployments. The access is hands off, the operator is not logged in to the kubernetes node to login to docker.
The process is the following:
- The deployments have an entry called “imagePullSecrets” immediately under the deployment entry, that has a name of a secret that contains the login information for docker
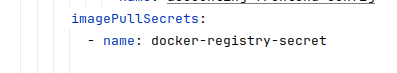
- The secret must be in the same namespace as the deployment
- The secret has the template below:
apiVersion: v1 kind: Secret metadata: name: docker-registry-secret namespace: cbox type: kubernetes.io/dockerconfigjson data: .dockerconfigjson: here
- dockerconfigjson does the magic: it contains the base64 depiction of the docker config.json mentioned above.
At AWS the token lasts a couple of good hours, so probably if you updated the docker registry secret, it is good to work with it for the whole day, however next day you will surely have to update it with fresh up to date info.