This shows how to configure reverse SSH having a linux machine on the cloud, exposing a port on that one that is forwarded on your home machine at a specified port.
The settings are two:
- one setting on the machine, allowing remote SSH to bind to all IP addresses when reverse is triggered, otherwise will only bind to loopback address (security feature)
- one setting on local machine, running windows and Putty to trigger the connection.
Remote Machine
On the remote machine assume you run Linux with sshd. Go to the settings file /etc/ssh/sshd_config and look for the setting called GatewayPorts, which can have three values
- off – for tunnel SSH only binds to localhost, that means the reverse connection port is only accessible from the remote machine itself
- on – forces bind to all IP addresses associated to the machine, which allows access from remote machines
- clientspecified – the client indicates to which IP address to bind for this particular setting
Do not forget to restart sshd after those changes are done
systemctl restart sshOK now on the machine, fire up Putty and first setup the connection as SSH connection and specify the remote machine address; the port is 22 usually.
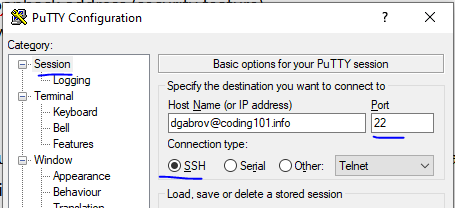
OK and now proceed to SSH / Tunnels
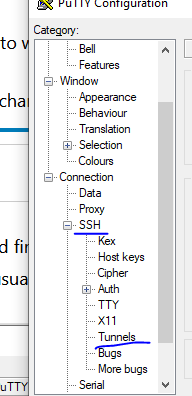
There, those are the settings:
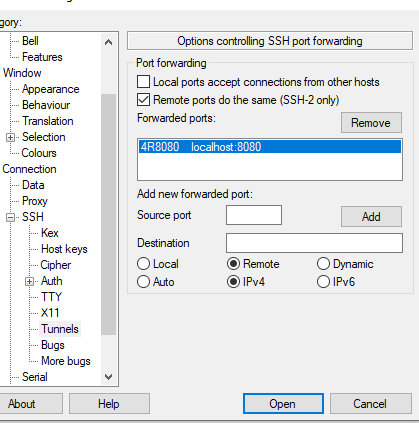
The entry is already configured, however
- select “remote ports do the same” although it is not used here
- Source port is the port where you connect on the remote machine
- Destination is localhost:port with the port on the local machine.
- Select Remote radio button (the R after 4 in the connection string). This is the most important setting.
- IPv4 would add that “4” in the connection string and will remove the IPV6 from the picture
A good thing is to go on the remote machine and ensure the port you want it to listen to is bound to all addresses, connect, su root and then run netstat -nat and here is what I see in my case:
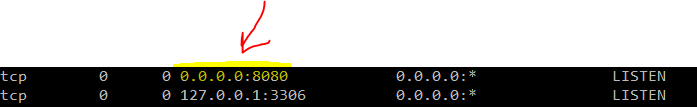
Clearly, 8080 bound to all the machine IPs